Full deets here:
https://www.kickstarter.com/blog/important-kickstarter-security-notice
Figured it's worth a mention here, 'cos apparently many of you have so much spare bucks to give to Zack Braff film-projects through this thing.
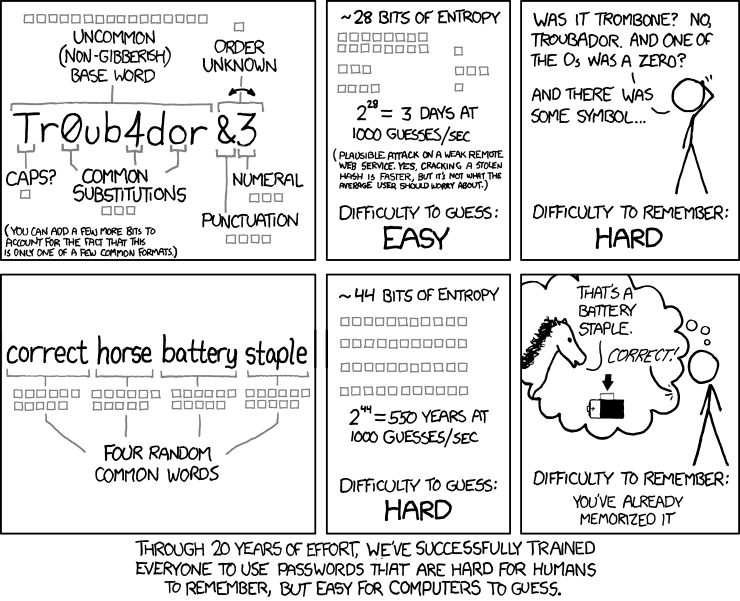
Change your password!
.
https://www.kickstarter.com/blog/important-kickstarter-security-notice
Figured it's worth a mention here, 'cos apparently many of you have so much spare bucks to give to Zack Braff film-projects through this thing.

Change your password!
.